SAFETY NEEDS ARE ON EVERY SIDE

SOLUTIONS END TO END FOR:
- AIRPORTS
- COMMERCIAL AREA
- MEDICAL CARE
- EDUCATION
- STADIUMS
- INFRAESTRUCTURA A CRÍTICA
- BANKS
- CASINOS
- RETAIL COMMERCE
- LOGISTICS
- PUBLIC TRANSIT
- VIDEO SURVEILLANCE OF CITIES
CCTV MONITORING SYSTEM
 1. Monitoring
1. Monitoring
- Evaluation and technical safety survey defined for each company.
- Installation of monitoring centers.
- Engineering and execution of security projects.
 3. Installation
3. Installation
- High definition security cameras.
- Security technical support
- Powerful video management and administration software.
 2. Camera
2. Camera
- Advice and sale of equipment.
- Video analytics with artificial intelligence (cameras capable of learning alone) that are shipped on the cameras.
- Intelligent and interoperable security solutions with other systems.
 4. Security
4. Security
- The fastest event and video search on the market.
- Unusual motion detection (UMD).
- Advanced artificial intelligence technology.
VIDEO DETECTION
-
Unusual motion detection (UMD) Advanced artificial intelligence technology
-
Unusual movement: continuously learn what normal activity looks like in a scene, and then point out unusual movements (eg, vehicle against traffic, person loitering or walking out of time, etc.)
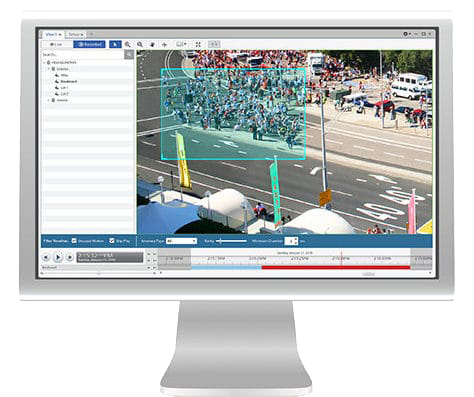
DIGITAL SECURITY TRANSFORMATION
We support the Control Centers to:
1) Be Proactive what is happening and act immediately.
2) Have a Forensic Test, fast obtaining evidence.

- Forensic search and investigation in minutes
- Resolution and level details (1‐29 Mpx).
- Minimum bandwidth (HDMS).
- Open, integrable, scalable, remote and multisite adminis.
- SW Easy to use, minimizes alerts and avoids activating protocol.
- Compatible with current IP and analog cameras.
- Speed and delivery of the best evidence.
 INTEGRATION OF THE CONTROL CENTER WITH ACCESS CONTROL SYSTEMS
INTEGRATION OF THE CONTROL CENTER WITH ACCESS CONTROL SYSTEMS
Alarm monitoring:
From access control events, activate alarms and synchronize with the Central: Door open / forced, Intrusion, Invalid / valid credential, lack of maintenance, system failure, sabotage.
Brand agnostic, operate with any camera
Extract, analyze and store face images directly from your surveillance video, the suspects being marked and inscribed on your blacklist.
Generate rule-based suspect notifications
Live video verification:
From the Central in front of access control alerts and / or to remotely manage door opening.
Rule Activation:
Activate alerts based on access control events.
Send notification via email.
Mark the video for later review.
Point the camera at a specific area of interest.
Manage roles and authorizations for physical access by zone / time.
Open architecture, being able to reuse your current access systems (card readers).
Plug & Play, immediate and scalable operation.
Special treatment for VIP identities.
Multisite solution with centralized administration.
High accuracy: 0.1% false positives.



